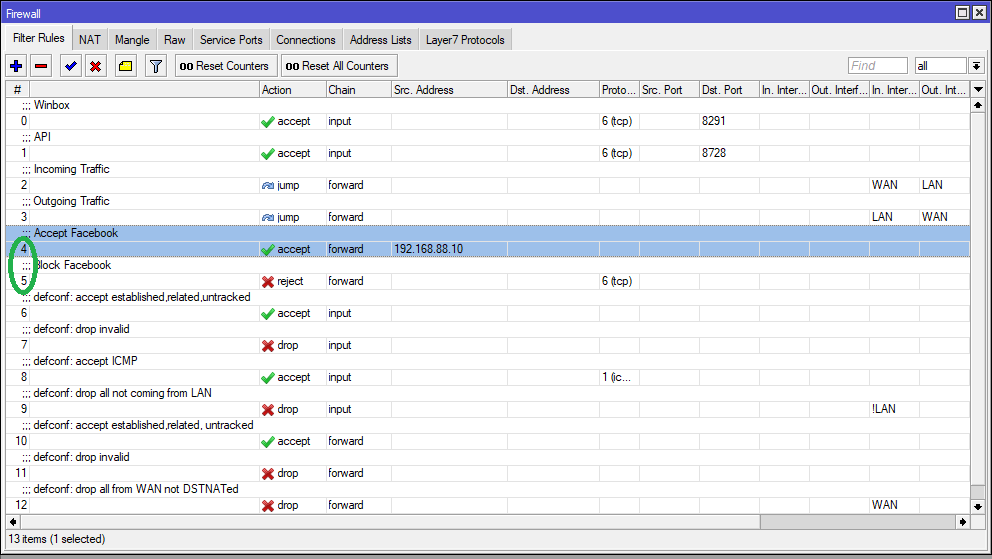
How to whitelist users to access blocked websites on Mikrotik
If a website is blocked across all networks, or on a certain network, but certain specific devices need to be given access to these sites, then we will create another filter rule and place it above the existing Website Blocking rule. The steps are as follows:
Let's assume first the network has blocked access to 'facebook' for all users and we are given the task to allow few devices/users to access facebook while access for others remain unchanged.
If a single device is to be given access to a blocked site, there are two methods through which this can be done:
Method 1: Whitelisting the device using the IP address (for example, a particular device is assigned 192.168.88.10 IP internally
In the 'IP>Firewall>Filter Rules' tab, Add a new rule '+'
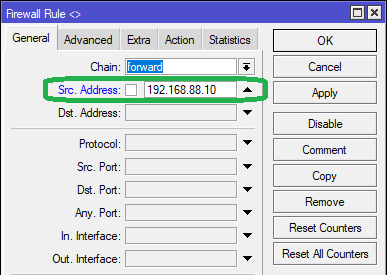
In the General tab, select chain as forward and Src. Address as the IP assigned to the device (192.168.88.10)
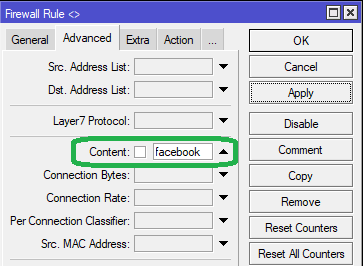
In the 'Advanced' Enter 'facebook' in the content field
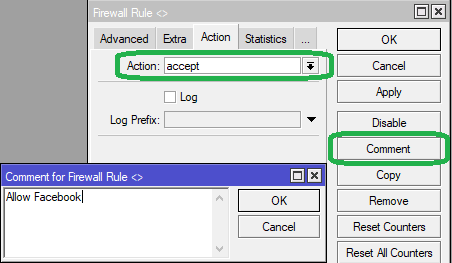
In the 'Actions' Enter accept in the Action field
Click on Comment to add a label "Allow Facebook" to the rule. Click Apply, then OK
The MikroTik terminal command for adding the above rule is as follows:
/ip firewall filter add chain=forward src-address="192.168.88.10" content="facebook" action=accept comment="Allow Facebook"
The rule needs to be placed above the "Block Facebook" rules added for the entire network.
Drag this rule above the Block Website filter rule.
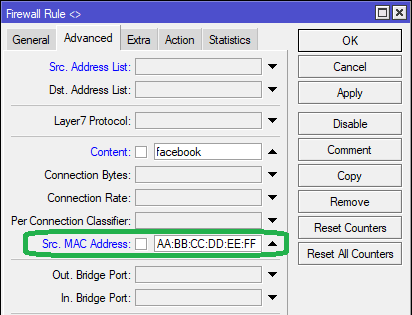
Method 2: Whitelisting the device using the MAC address (AA:BB:CC:DD:EE:FF)
In the 'IP>Firewall>Filter Rules' tab, Add a new rule '+'
In the General tab, select chain as forward
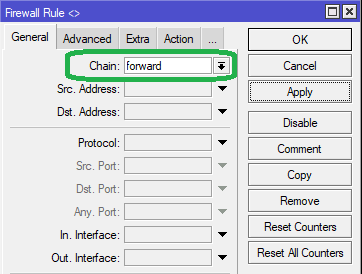
In the 'Advanced' Enter 'facebook' in the content field
In the Src. MAC Addressfield, enter the MAC address of the ddevice as seen below.
In the 'Actions' Enter accept in the Action field
Click on Comment to add a label "Allow Facebook" to the rule. Click Apply, then OK

The MikroTik terminal command for adding the above rule is as follows:
/ip firewall filter add chain=forward src-mac-address="AA-BB-CC-DD-EE-FF" content="facebook" action=accept comment="Allow Facebook"
The rule needs to be placed above the "Block Facebook" rules added for the entire network.
If a bunch of devices are to be collectively white-listed for accessing a blocked website, then those devices will need to be manually assigned IP addresses, preferably outside the DHCP pool range, either directly on the devices itself, or through MikroTik using DHCP Static Leases.
Assuming a website is blocked on an entire network, say 192.168.88.0/24, and devices assigned IP addresses 192.168.88.2-192.168.88.9 need to be white-listed, this is how it can be done:
In the 'IP>Firewall>Filter Rules' tab, Add a new rule '+'
In the General tab, select chain as forward
In Src. Address, we specify the IP range of the devices as seen below:
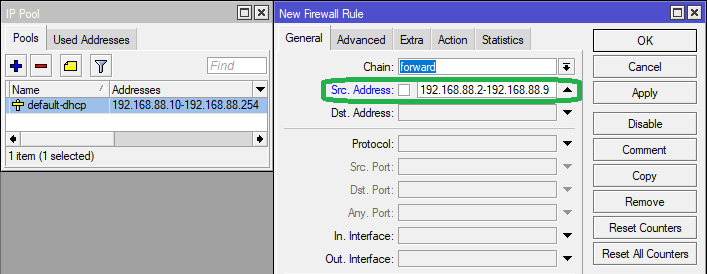
In the 'Advanced' Enter 'facebook' in the content field

In the 'Actions' Enter accept in the Action field
Click on Comment to add a label "Allow Facebook" to the rule. Click Apply, then OK

The MikroTik terminal command for adding the above rule is as follows:
/ip firewall filter add chain=forward src-address="192.168.88.2-192.168.88.9" content="facebook" action=accept comment="Allow Facebook"
The rule needs to be placed above the "Block Facebook" rules added for the entire network.
Drag this rule above the Block Website filter rule.

Thus, the “Allow Website” rule created here will allow the website to be accessed by the specific devices decided as per the three conditions mentioned above, while the website will remain blocked for the rest of the devices on the network.
If you are not sure how to block websites for entire network through Filter Rules, you can read below FAQ for more details
How to block websites through filter rules in Mikrotik